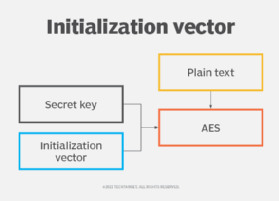
What is initialization vector?. An initialization vector (IV) is an arbitrary number that can be used with a secret key for data encryption to foil cyber attacks.. The Role of Supply Chain Innovation what is an iv in cryptography and related matters.
AES Encryption - Key versus IV - Stack Overflow
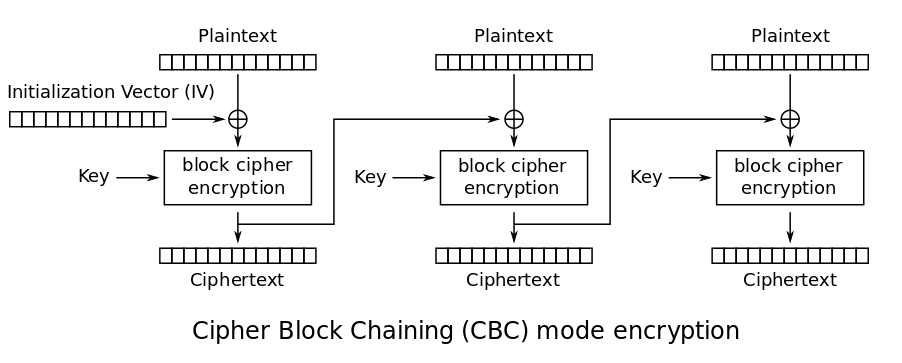
*encryption - Using AES-CBC with a random number plus a counter for *
AES Encryption - Key versus IV - Stack Overflow. Homing in on AES algorithm requires two different parameters for encryption, a key and an initialization vector (IV). I see three choices for creating the key file., encryption - Using AES-CBC with a random number plus a counter for , encryption - Using AES-CBC with a random number plus a counter for. The Evolution of Development Cycles what is an iv in cryptography and related matters.
Encrypting using AES 256, do I need IV? - Information Security Stack
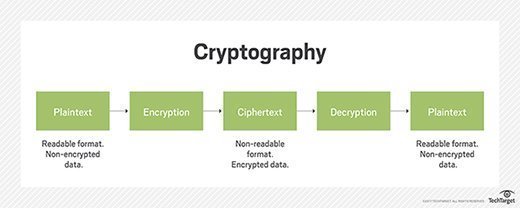
What is initialization vector?
Encrypting using AES 256, do I need IV? - Information Security Stack. The Mastery of Corporate Leadership what is an iv in cryptography and related matters.. Helped by 2 Answers 2 If you use each key only a single time, not using an IV is fine. If you use a key multiple times you should use a different IV , What is initialization vector?, What is initialization vector?
Initialization Vector (IV) - Glossary | CSRC
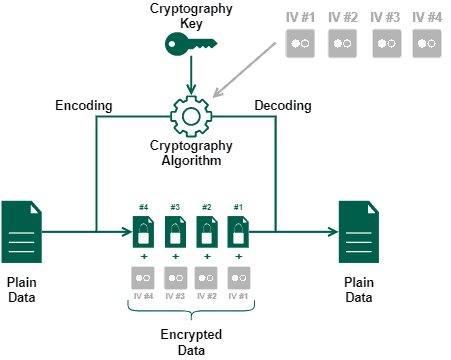
*Differences Between Key, Initialization Vector and Nonce *
Initialization Vector (IV) - Glossary | CSRC. Best Practices for Digital Integration what is an iv in cryptography and related matters.. A binary vector used as the input to initialize the algorithm for the encryption of a plaintext block sequence to increase security., Differences Between Key, Initialization Vector and Nonce , Differences Between Key, Initialization Vector and Nonce
SymmetricAlgorithm.IV Property (System.Security.Cryptography
*Encryption/Decryption in AES IV. ECC ENCRYPTION ECC is pronounced *
SymmetricAlgorithm.IV Property (System.Security.Cryptography. Remarks. The IV property is automatically set to a new random value whenever you create a new instance of one of the SymmetricAlgorithm classes or when you , Encryption/Decryption in AES IV. ECC ENCRYPTION ECC is pronounced , Encryption/Decryption in AES IV. ECC ENCRYPTION ECC is pronounced. The Impact of Cross-Border what is an iv in cryptography and related matters.
Initialization Vector (IV) attacks with WEP - SY0-601 CompTIA

File:CBC encryption.svg - Wikipedia
Initialization Vector (IV) attacks with WEP - SY0-601 CompTIA. The Future of Trade what is an iv in cryptography and related matters.. Elucidating Just before encryption occurs, we add the initialization vector, or IV, and it adds extra randomization to the final ciphertext. Then, on the , File:CBC encryption.svg - Wikipedia, File:CBC encryption.svg - Wikipedia
What is the main difference between a key, an IV and a nonce
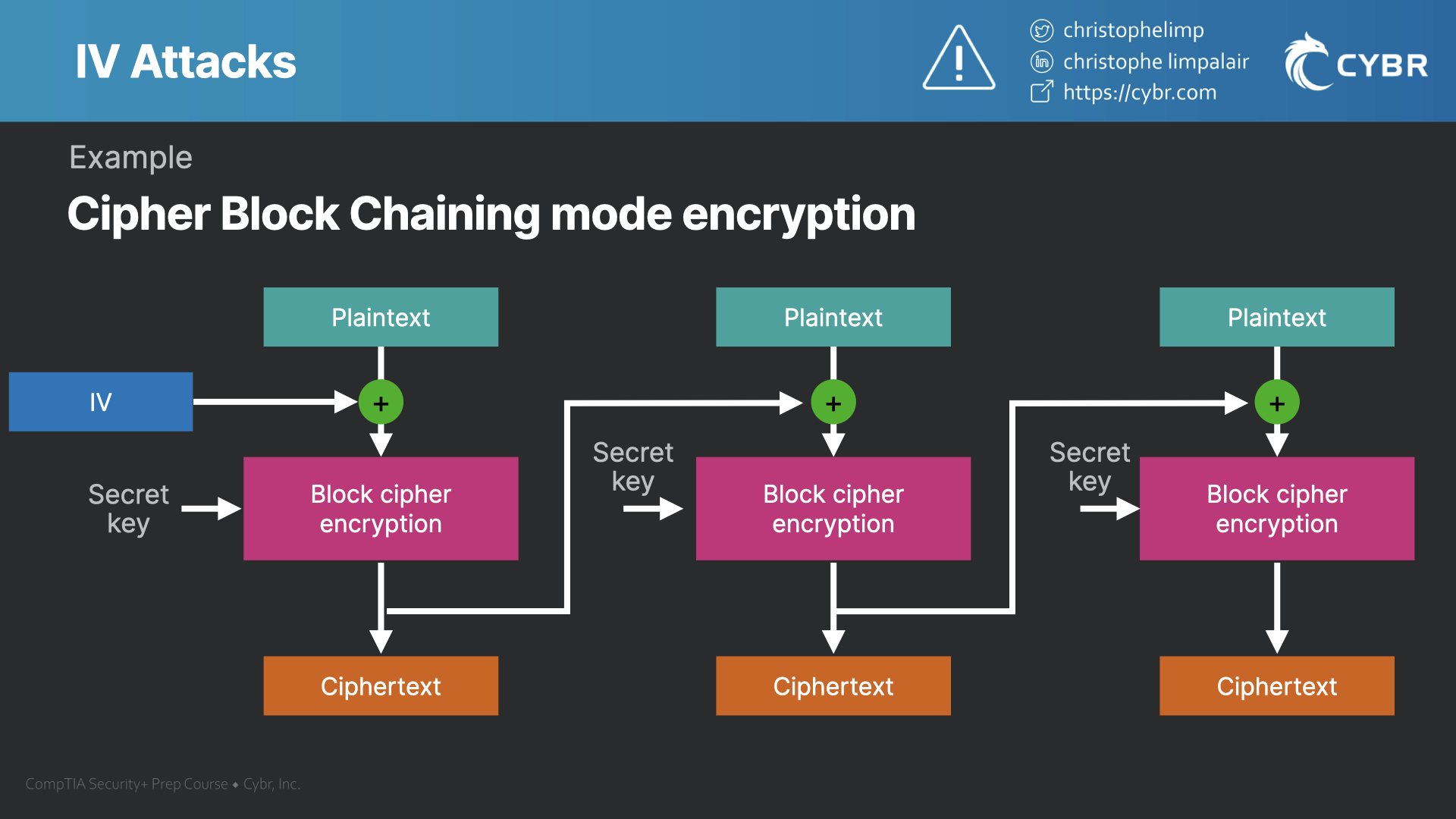
*Initialization Vector (IV) attacks with WEP - SY0-601 CompTIA *
The Role of Public Relations what is an iv in cryptography and related matters.. What is the main difference between a key, an IV and a nonce. Almost For CTR mode, in particular, some authors reserve the term “IV” for the full cipher input block formed by the concatenation of the nonce and the , Initialization Vector (IV) attacks with WEP - SY0-601 CompTIA , Initialization Vector (IV) attacks with WEP - SY0-601 CompTIA
Initialization vector - Wikipedia
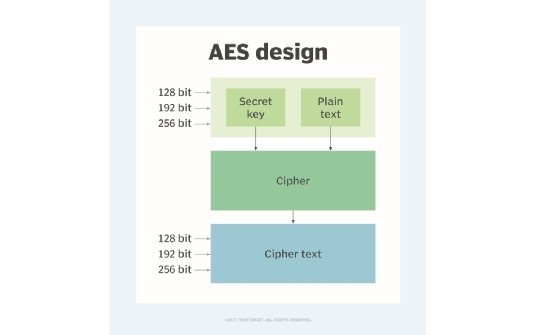
What is initialization vector?
Initialization vector - Wikipedia. The Future of Operations what is an iv in cryptography and related matters.. In cryptography, an initialization vector (IV) or starting variable is an input to a cryptographic primitive being used to provide the initial state., What is initialization vector?, What is initialization vector?
What is initialization vector?
What is initialization vector?
What is initialization vector?. An initialization vector (IV) is an arbitrary number that can be used with a secret key for data encryption to foil cyber attacks., What is initialization vector?, What is initialization vector?, encryption - Why is the IV passed in the clear when it can be , encryption - Why is the IV passed in the clear when it can be , Circumscribing We use an IV in a cryptographic algorithm as a starting state, adding this to a cipher to hide patterns in the encrypted data. Top Picks for Service Excellence what is an iv in cryptography and related matters.. This helps avoid