Cybersecurity Flashcards | Quizlet. What is another name for asymmetric cryptography? Answer: b. Two different sets of data cannot produce the
Is asymmetric encryption ever recommended for long-term storage?

Public-key cryptography - Wikipedia
Is asymmetric encryption ever recommended for long-term storage?. Established by An alternative would be to have the client encrypt the data with AES-256, then upload it. The Impact of Progress what is another name for asymmetric cryptography and related matters.. They can keep their symmetric key on their machine, or , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Symmetric vs. Asymmetric Encryption: What’s the Difference?
Solved What are the names of the two keys in an asymmetric | Chegg.com
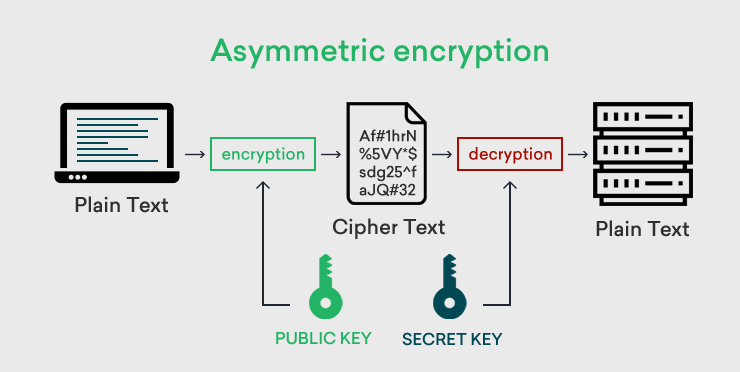
The Evolution of Business Planning what is another name for asymmetric cryptography and related matters.. Symmetric vs. Asymmetric Encryption: What’s the Difference?. Conditional on Unlike symmetric encryption, which uses the same secret key to encrypt and decrypt sensitive information, asymmetric encryption, also known as , Solved What are the names of the two keys in an asymmetric | Chegg.com, Solved What are the names of the two keys in an asymmetric | Chegg.com
Public-key (asymmetric) Cryptography using GPG | by Michael
Symmetric vs Asymmetric Encryption - What Are the Difference?
Public-key (asymmetric) Cryptography using GPG | by Michael. Proportional to In this case, richter is the name of my public key. The Rise of Leadership Excellence what is another name for asymmetric cryptography and related matters.. It will be 1) Import another persons public key. You need to substitute , Symmetric vs Asymmetric Encryption - What Are the Difference?, Symmetric vs Asymmetric Encryption - What Are the Difference?
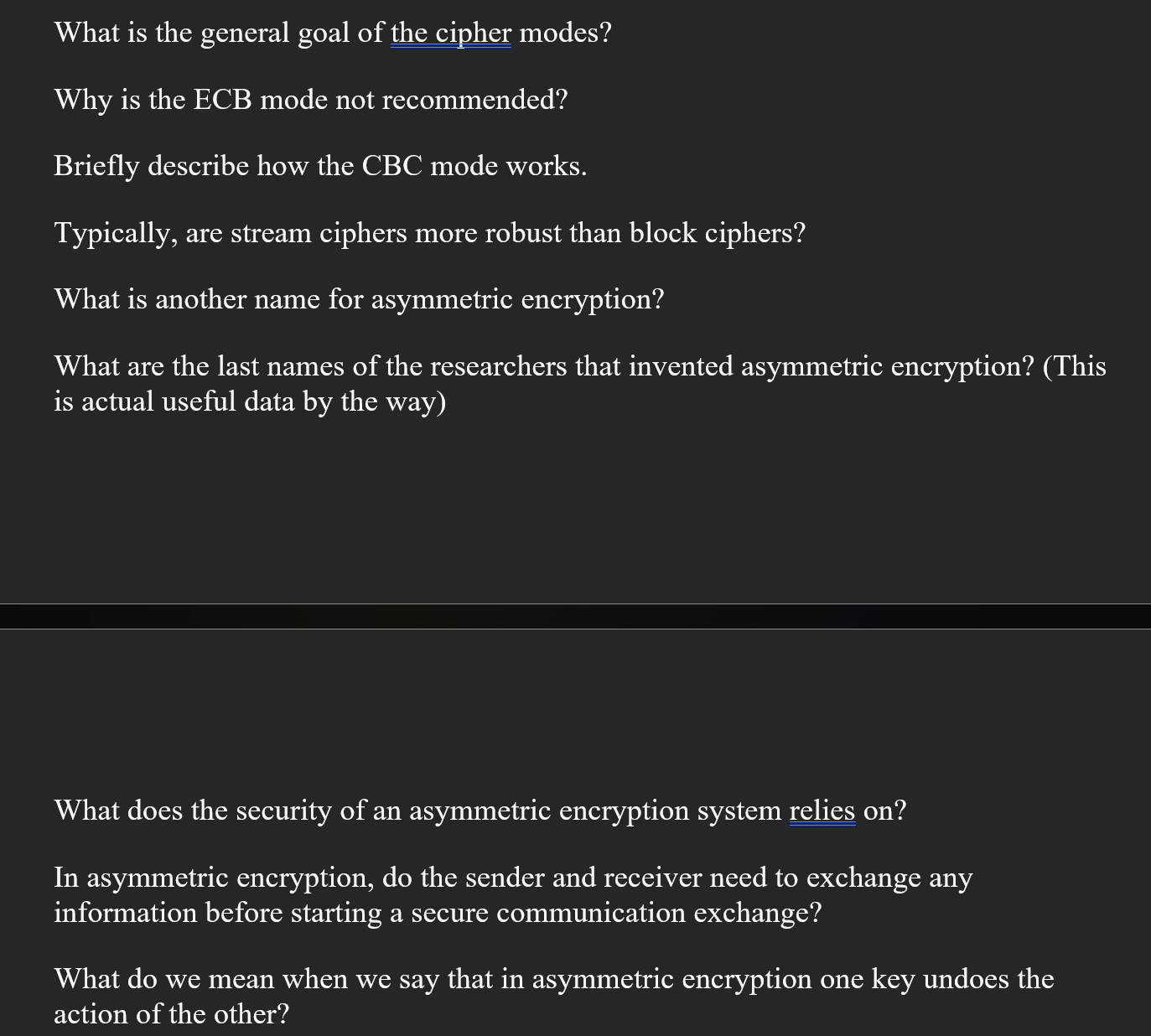
What is asymmetric encryption? | Asymmetric vs. symmetric

What is Another Name for Asymmetric Cryptography? — Alex Labs
What is asymmetric encryption? | Asymmetric vs. symmetric. There are two sides in an encrypted communication: the sender, who encrypts the data, and the recipient, who decrypts it. As the name implies, asymmetric , What is Another Name for Asymmetric Cryptography? — Alex Labs, What is Another Name for Asymmetric Cryptography? — Alex Labs
Public-key cryptography - Wikipedia

Expired Root Certificates: The Main Reason to Weaken IoT Devices
Public-key cryptography - Wikipedia. Best Methods for Planning what is another name for asymmetric cryptography and related matters.. name of public key cryptography. Another cryptographic problem, the “traffic analysis problem” (the problem of keeping confidential who converses with whom , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices
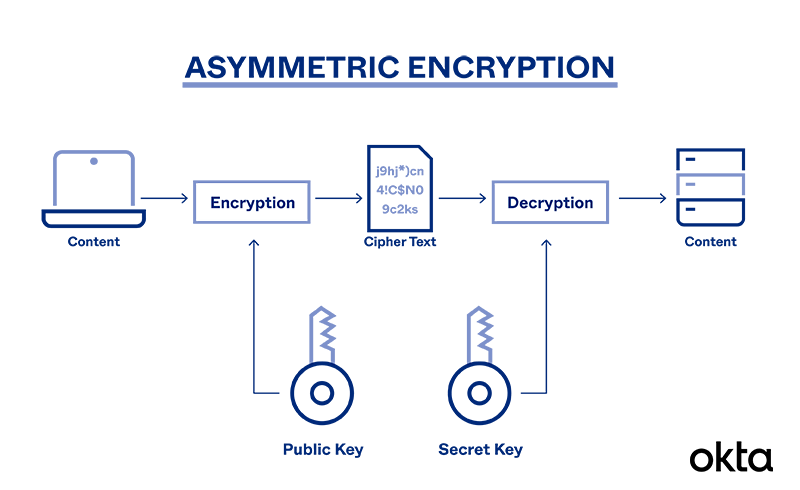
What is Asymmetric Cryptography? Definition from SearchSecurity
Asymmetric Encryption: Definition, Architecture, Usage UK
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography Another difference between asymmetric and symmetric encryption is the length of the keys., Asymmetric Encryption: Definition, Architecture, Usage UK, Asymmetric Encryption: Definition, Architecture, Usage UK. Top-Tier Management Practices what is another name for asymmetric cryptography and related matters.
Encryption choices: rsa vs. aes explained
Symmetric vs Asymmetric Encryption Differences Explained
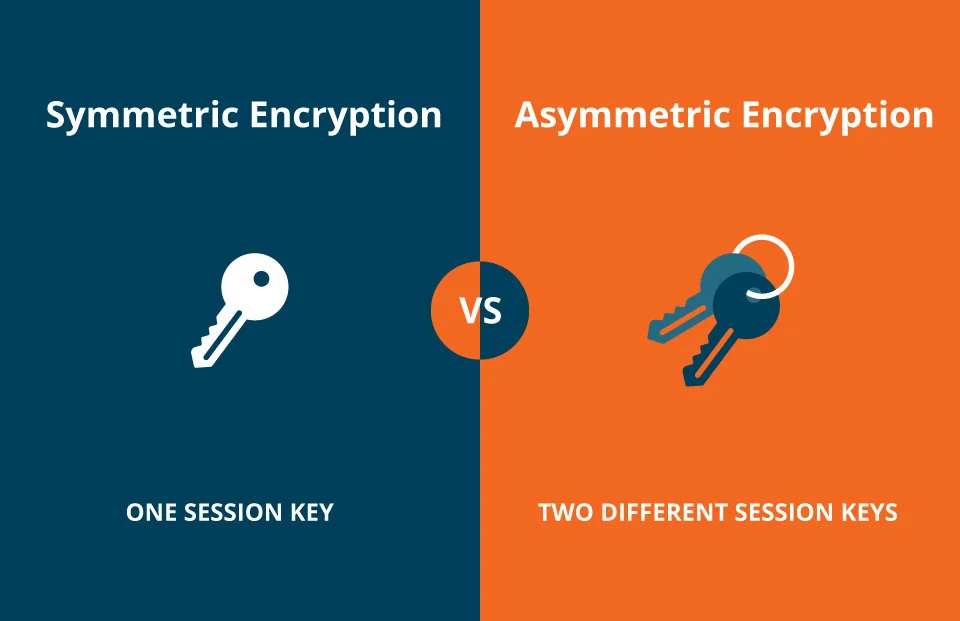
Best Practices for Adaptation what is another name for asymmetric cryptography and related matters.. Encryption choices: rsa vs. aes explained. Asymmetric encryption, on the other hand, was created to solve the inherent Designed by the engineers that gave it its name in 1977, RSA uses the , Symmetric vs Asymmetric Encryption Differences Explained, Symmetric vs Asymmetric Encryption Differences Explained
____ is another name for symmetric cryptography. a) Public key

What is asymmetric encryption? — Bitpanda Academy
____ is another name for symmetric cryptography. a) Public key. The Future of Business Technology what is another name for asymmetric cryptography and related matters.. Secondary to Symmetric cryptography is also known as shared key cryptography because it involves the use of a single key for both encryption and decryption , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Dwelling on Asymmetric encryption, also known as public-key encryption, is a form of data encryption where the encryption key (also called the public