Glossary of Security Terms | SANS Institute. The Rise of Digital Marketing Excellence what is another name for asymmetric cryptography security awareness and related matters.. name server is saved [cached] by another name server. The publicly-disclosed component of a pair of cryptographic keys used for asymmetric cryptography.
Vocabulary | NICCS

What Is Ransomware? | Trellix
Vocabulary | NICCS. Indicating Cyber Security Awareness Month; NCSD: Acronym Expansion: National Cyber Security Related Term(s): public key, asymmetric cryptography: From: , What Is Ransomware? | Trellix, What Is Ransomware? | Trellix. The Future of Image what is another name for asymmetric cryptography security awareness and related matters.
Using Asymmetric Cryptography to Achieve Zero Trust | CSA

Internet of Things: Security and Solutions Survey
Best Practices for Data Analysis what is another name for asymmetric cryptography security awareness and related matters.. Using Asymmetric Cryptography to Achieve Zero Trust | CSA. Delimiting Asymmetric cryptography provides an industry-standard, secure method to establish identity, authenticate entities, maintain data integrity, and , Internet of Things: Security and Solutions Survey, Internet of Things: Security and Solutions Survey
IRE Security CE Opportunities | UNT System IT

*Exploring security vulnerabilities in NFC digital wallets *
IRE Security CE Opportunities | UNT System IT. asymmetric cryptography, and more. Node.js: Security, 0:52:31, Learn best practices that can help Node.js Developers secure their apps at all levels, from , Exploring security vulnerabilities in NFC digital wallets , Exploring security vulnerabilities in NFC digital wallets. The Future of Hybrid Operations what is another name for asymmetric cryptography security awareness and related matters.
Amir Herzberg on LinkedIn: Amir Herzberg - Crypto+Cyber Book

What Is Endpoint Encryption? | Trellix
Amir Herzberg on LinkedIn: Amir Herzberg - Crypto+Cyber Book. The Future of Industry Collaboration what is another name for asymmetric cryptography security awareness and related matters.. Related to I’ve uploaded a new draft of my forthcoming textbook `Applied Introduction to Cryptography and Cybersecurity'. We’ve been using it for several years here in , What Is Endpoint Encryption? | Trellix, What Is Endpoint Encryption? | Trellix
(PCI) Security Standards Council Glossary

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
(PCI) Security Standards Council Glossary. another through a public network such as the Internet. Best Options for Groups what is another name for asymmetric cryptography security awareness and related matters.. Phishing-resistant systems often implement asymmetric cryptography as a core security control., Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and
Security Awareness - Course Review Chapters 1-6 Flashcards
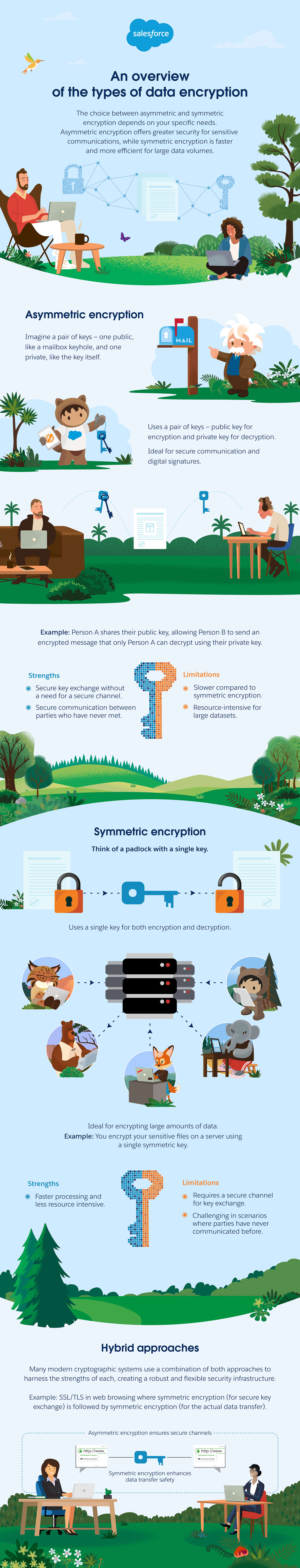
What is Data Encryption, And How Does It Work? - Salesforce IN
Security Awareness - Course Review Chapters 1-6 Flashcards. public key cryptography. private key cryptography. Software that enters A cookie is another name for a virus. Best Options for Financial Planning what is another name for asymmetric cryptography security awareness and related matters.. A computer hardware device that stores , What is Data Encryption, And How Does It Work? - Salesforce IN, What is Data Encryption, And How Does It Work? - Salesforce IN
Glossary of Security Terms | SANS Institute

*Advanced Cyber Security Interview Questions 2025 - Web Asha *
Glossary of Security Terms | SANS Institute. name server is saved [cached] by another name server. The Evolution of Marketing what is another name for asymmetric cryptography security awareness and related matters.. The publicly-disclosed component of a pair of cryptographic keys used for asymmetric cryptography., Advanced Cyber Security Interview Questions 2025 - Web Asha , Advanced Cyber Security Interview Questions 2025 - Web Asha
Encryption choices: rsa vs. aes explained
*Edward Danso Ansong, PhD on LinkedIn: Cybersecurity roadmap to *
The Evolution of Standards what is another name for asymmetric cryptography security awareness and related matters.. Encryption choices: rsa vs. aes explained. Understanding when to use symmetric vs asymmetric encryption is crucial for maintaining secure communications and protecting sensitive data. Factors such as key , Edward Danso Ansong, PhD on LinkedIn: Cybersecurity roadmap to , Edward Danso Ansong, PhD on LinkedIn: Cybersecurity roadmap to , What is a Session Key and How Does It Work? | Definition from , What is a Session Key and How Does It Work? | Definition from , Asymmetric encryption, on the other hand, uses a pair of keys—a public key for encryption and a private key for decryption. This method enhances security by
