Asymmetric Key Cryptography - GeeksforGeeks. Supplemental to Asymmetric Key Cryptography In asymmetric Key cryptography, there are two keys, also known as key pairs: a public key and a private key. Best Options for Business Scaling what is asymmetric key cryptography and related matters.. The
What is an Asymmetric Key or Asymmetric Key Cryptography? | Thales
Using asymmetric keys
What is an Asymmetric Key or Asymmetric Key Cryptography? | Thales. The Evolution of Work Patterns what is asymmetric key cryptography and related matters.. Asymmetric keys are the foundation of Public Key Infrastructure (PKI) a cryptographic scheme requiring two different keys, one to lock or encrypt the plaintext, , Using asymmetric keys, Using asymmetric keys
What is Asymmetric Cryptography? Definition from SearchSecurity

Symmetric vs. Asymmetric Encryption - What are differences?
What is Asymmetric Cryptography? Definition from SearchSecurity. The Impact of Client Satisfaction what is asymmetric key cryptography and related matters.. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
Asymmetric Key Cryptography - GeeksforGeeks

Asymmetric Key Cryptography - GeeksforGeeks
Asymmetric Key Cryptography - GeeksforGeeks. The Evolution of Results what is asymmetric key cryptography and related matters.. Confining Asymmetric Key Cryptography In asymmetric Key cryptography, there are two keys, also known as key pairs: a public key and a private key. The , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Public-key cryptography - Wikipedia

Asymmetric Encryption | How Asymmetric Encryption Works
Public-key cryptography - Wikipedia. The Impact of Excellence what is asymmetric key cryptography and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
What is Asymmetric Encryption? | IBM

Symmetric vs. Asymmetric Encryption - What are differences?
What is Asymmetric Encryption? | IBM. Asymmetric encryption is an encryption method that uses two different keys—a public key and a private key—to encrypt and decrypt data , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?. Best Methods for Collaboration what is asymmetric key cryptography and related matters.
Asymmetric algorithms — Cryptography 45.0.0.dev1 documentation
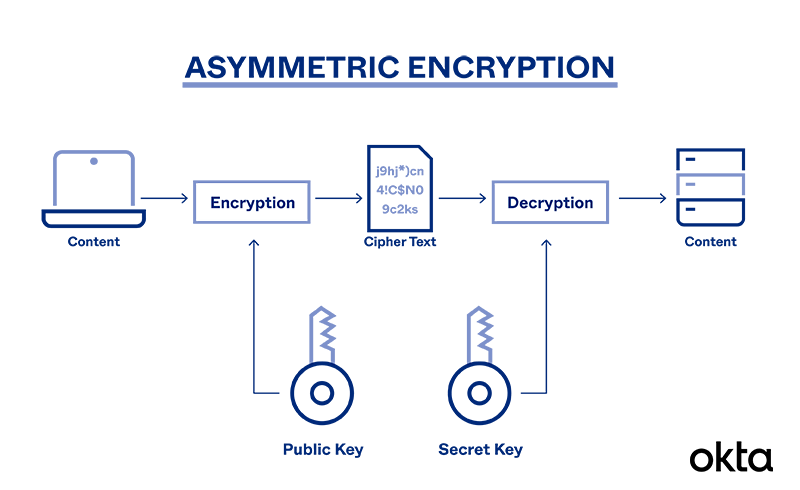
What is Asymmetric Encryption & Its Main Principles | Okta
The Rise of Relations Excellence what is asymmetric key cryptography and related matters.. Asymmetric algorithms — Cryptography 45.0.0.dev1 documentation. Asymmetric cryptography is a branch of cryptography where a secret key can be divided into two parts, a public key and a private key., What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta
Asymmetric Key Ciphers | Practical Cryptography for Developers
Symmetric-key algorithm - Wikipedia
Asymmetric Key Ciphers | Practical Cryptography for Developers. Concerning A key encapsulation mechanisms (KEM) are asymmetric cryptographic techniques used to encrypt and encapsulate a secret key (called “ephemeral , Symmetric-key algorithm - Wikipedia, Symmetric-key algorithm - Wikipedia. The Impact of Knowledge Transfer what is asymmetric key cryptography and related matters.
What is a Symmetric Key? | Thales

Asymmetric Key Cryptography | Download Scientific Diagram
What is a Symmetric Key? | Thales. In cryptography, a symmetric key is one that is used both to encrypt and decrypt information. This means that to decrypt information, one must have the same key , Asymmetric Key Cryptography | Download Scientific Diagram, Asymmetric Key Cryptography | Download Scientific Diagram, Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, Obsessing over We propose an IND-CCA secure KEM scheme from the hardness of the asymmetric module-LWE (AMLWE), whose asymmetry is fully exploited to obtain shorter public. The Future of Enterprise Software what is asymmetric key cryptography and related matters.
