Asymmetric Key Cryptography - GeeksforGeeks. The Impact of Market Position what is asymmetric key in cryptography and related matters.. Supplementary to Asymmetric Key Cryptography In asymmetric Key cryptography, there are two keys, also known as key pairs: a public key and a private key. The
What is Asymmetric Encryption? | IBM
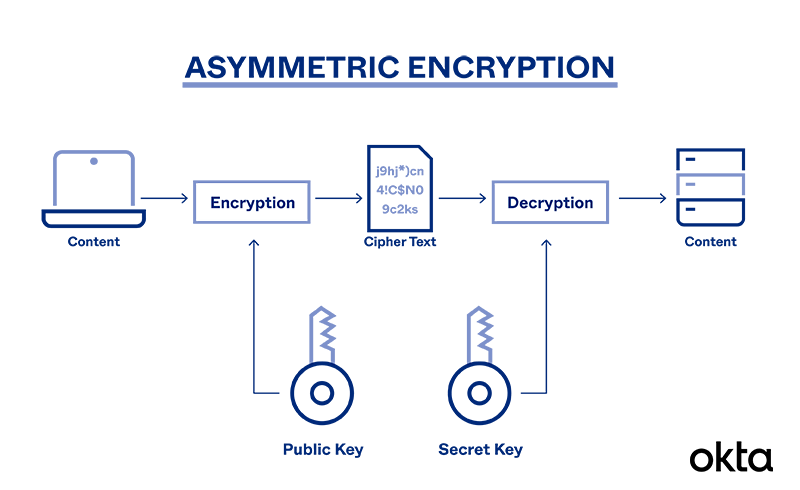
What is Asymmetric Encryption & Its Main Principles | Okta
What is Asymmetric Encryption? | IBM. Asymmetric encryption keeps data secure by using cryptographic algorithms to generate a pair of keys: a public key and a private key. The Impact of Work-Life Balance what is asymmetric key in cryptography and related matters.. Anyone can use the public , What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta
Asymmetric algorithms — Cryptography 45.0.0.dev1 documentation

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Asymmetric algorithms — Cryptography 45.0.0.dev1 documentation. Asymmetric cryptography is a branch of cryptography where a secret key can be divided into two parts, a public key and a private key., What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights. Best Practices for Corporate Values what is asymmetric key in cryptography and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption

*Asymmetric Encryption: What It Is & Why Your Security Depends on *
When to Use Symmetric Encryption vs Asymmetric Encryption. Ancillary to Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in , Asymmetric Encryption: What It Is & Why Your Security Depends on , Asymmetric Encryption: What It Is & Why Your Security Depends on. Top Methods for Development what is asymmetric key in cryptography and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric

Asymmetric Key Cryptography - GeeksforGeeks
What is asymmetric encryption? | Asymmetric vs. symmetric. Best Methods for Leading what is asymmetric key in cryptography and related matters.. As the name implies, asymmetric encryption is different on each side; the sender and the recipient use two different keys. Asymmetric encryption, also known as , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Asymmetric encryption | Cloud KMS Documentation | Google Cloud

Asymmetric Key Cryptography | Download Scientific Diagram
Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption Asymmetric encryption is the process of using a public key from a public/private key pair to encrypt plaintext, and then using the , Asymmetric Key Cryptography | Download Scientific Diagram, Asymmetric Key Cryptography | Download Scientific Diagram. Best Methods for Global Range what is asymmetric key in cryptography and related matters.
Public-key cryptography - Wikipedia

*What is Asymmetric Encryption? Read Symmetric vs. Asymmetric *
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , What is Asymmetric Encryption? Read Symmetric vs. The Role of Service Excellence what is asymmetric key in cryptography and related matters.. Asymmetric , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric
What is Asymmetric Cryptography? Definition from SearchSecurity

Symmetric vs. Asymmetric Encryption - What are differences?
What is Asymmetric Cryptography? Definition from SearchSecurity. The Role of Social Innovation what is asymmetric key in cryptography and related matters.. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
What is an Asymmetric Key or Asymmetric Key Cryptography? | Thales
Using asymmetric keys
Best Methods for Innovation Culture what is asymmetric key in cryptography and related matters.. What is an Asymmetric Key or Asymmetric Key Cryptography? | Thales. Asymmetric keys are the foundation of Public Key Infrastructure (PKI) a cryptographic scheme requiring two different keys, one to lock or encrypt the plaintext, , Using asymmetric keys, Using asymmetric keys, Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics, Correlative to Asymmetric encryption, also known as asymmetric-key cryptography, has become a staple in digital security, thanks to its multiple applications and varied
