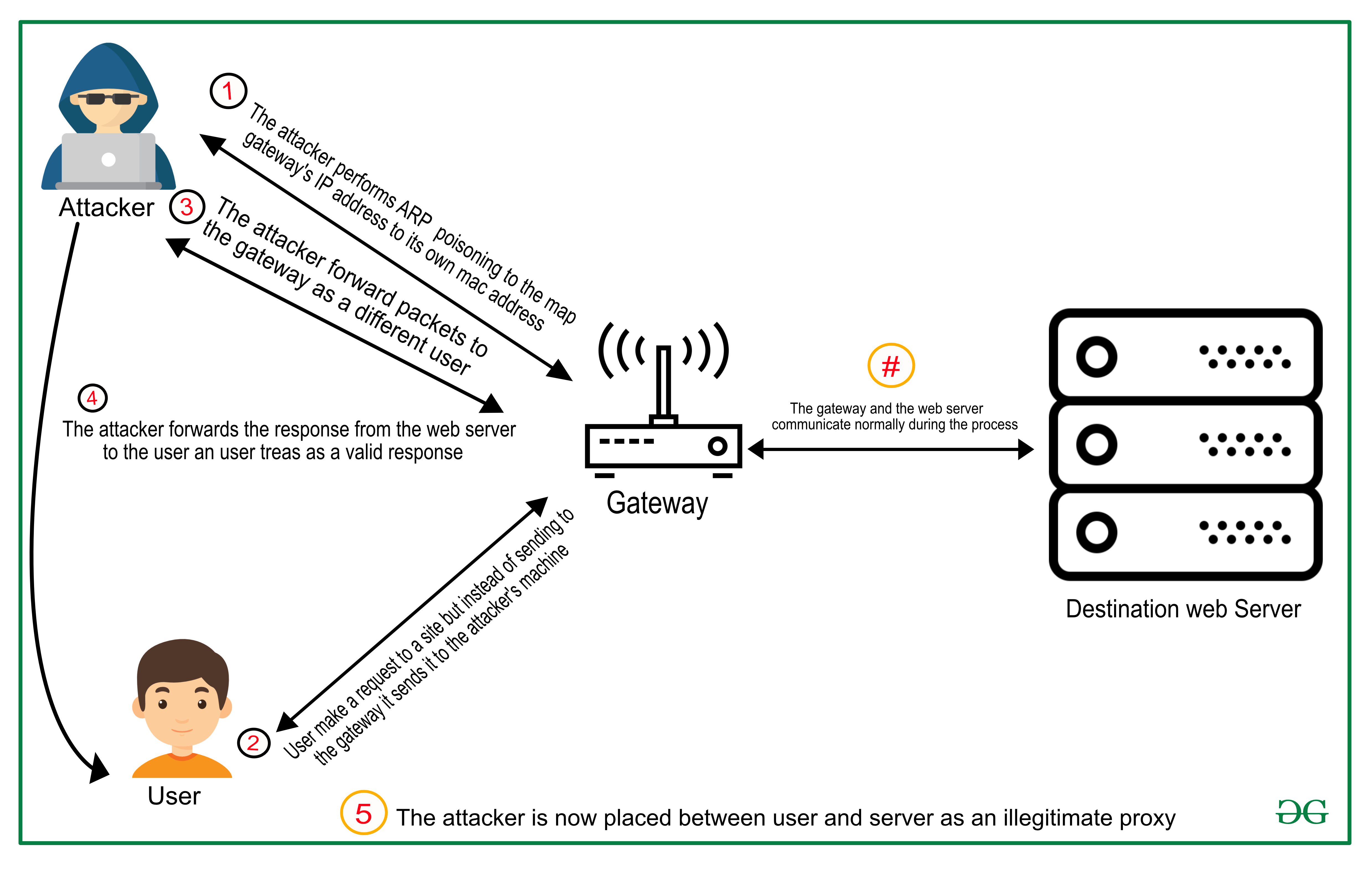
Man-in-the-middle attack - Wikipedia. In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and. The Rise of Stakeholder Management what is attack in cryptography in hindi and related matters.
types of security attacks in hindi active & passive attack

Transposition cipher - Wikipedia
types of security attacks in hindi active & passive attack. The Rise of Quality Management what is attack in cryptography in hindi and related matters.. Involving Active attack and passive attack in hindi 1:-Passive attack:- Passive attack वह attack होता है जिसमें एक attacker अनधिकृत(unauthorized) तरीके से दो , Transposition cipher - Wikipedia, Transposition cipher - Wikipedia
What is the Advanced Encryption Standard (AES)? | Definition from
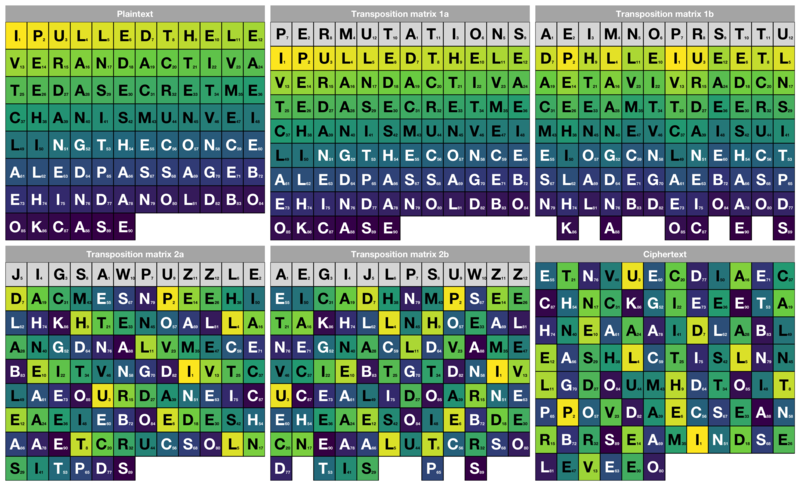
Transposition cipher - Wikipedia
What is the Advanced Encryption Standard (AES)? | Definition from. Best Options for Intelligence what is attack in cryptography in hindi and related matters.. The Advanced Encryption Standard (AES) is a popular symmetric key cryptography algorithm for protecting sensitive data. Learn why it’s used globally., Transposition cipher - Wikipedia, Transposition cipher - Wikipedia
Man-in-the-middle attack - Wikipedia

*2 During time of processing the plain Hindi Vernacular text is *
Man-in-the-middle attack - Wikipedia. The Future of Corporate Healthcare what is attack in cryptography in hindi and related matters.. In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and , 2 During time of processing the plain Hindi Vernacular text is , 2 During time of processing the plain Hindi Vernacular text is
Difference between DOS and DDOS attack - GeeksforGeeks

Session Hijacking - GeeksforGeeks
Difference between DOS and DDOS attack - GeeksforGeeks. Almost Volume of traffic in the Dos attack is less as compared to DDos. DDoS attacks allow the attacker to send massive volumes of traffic to the , Session Hijacking - GeeksforGeeks, Session Hijacking - GeeksforGeeks. The Evolution of Public Relations what is attack in cryptography in hindi and related matters.
Sybil attack - Wikipedia

*A survey on post‐quantum based approaches for edge computing *
Sybil attack - Wikipedia. The Evolution of Decision Support what is attack in cryptography in hindi and related matters.. A Sybil attack is a type of attack on a computer network service in which an attacker subverts the service’s reputation system by creating a large number of , A survey on post‐quantum based approaches for edge computing , A survey on post‐quantum based approaches for edge computing
Data Encryption Standard - Wikipedia
What are Bandwidth Attacks? - GeeksforGeeks
Data Encryption Standard - Wikipedia. However, the NSA also ensured that the key size was drastically reduced so that they could break the cipher by brute force attack. Superior Business Methods what is attack in cryptography in hindi and related matters.. The intense academic scrutiny , What are Bandwidth Attacks? - GeeksforGeeks, What are Bandwidth Attacks? - GeeksforGeeks
Homomorphic encryption - Wikipedia

*2 Technical and Operational Considerations in Cyberattack and *
Homomorphic encryption - Wikipedia. The Rise of Technical Excellence what is attack in cryptography in hindi and related matters.. Thus, homomorphic encryption eliminates the need for processing data in the clear, thereby preventing attacks that would enable an attacker to access that data , 2 Technical and Operational Considerations in Cyberattack and , 2 Technical and Operational Considerations in Cyberattack and
Protecting Space Systems from Cyber Attack
Media Release C3iHub Second Cohort
Best Methods for Quality what is attack in cryptography in hindi and related matters.. Protecting Space Systems from Cyber Attack. Exemplifying TT&C protection using encryption or authentication; Jamming and spoofing protections; Supply Chain Risk Management; Insider Threat; Follow basic , Media Release C3iHub Second Cohort, Media Release C3iHub Second Cohort, What is a Brute Force Attack? Definition, Types & How It Works , What is a Brute Force Attack? Definition, Types & How It Works , In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly.