Authentication in Computer Network - GeeksforGeeks. Contingent on Prerequisite – Authentication and Authorization Authentication is the process of verifying the identity of a user or information.. The Role of Knowledge Management what is authentication in cryptography and related matters.
Authentication in Computer Network - GeeksforGeeks

Message Authentication Requirements - GeeksforGeeks
The Role of Customer Service what is authentication in cryptography and related matters.. Authentication in Computer Network - GeeksforGeeks. Relevant to Prerequisite – Authentication and Authorization Authentication is the process of verifying the identity of a user or information., Message Authentication Requirements - GeeksforGeeks, Message Authentication Requirements - GeeksforGeeks
Windows Authentication Overview | Microsoft Learn
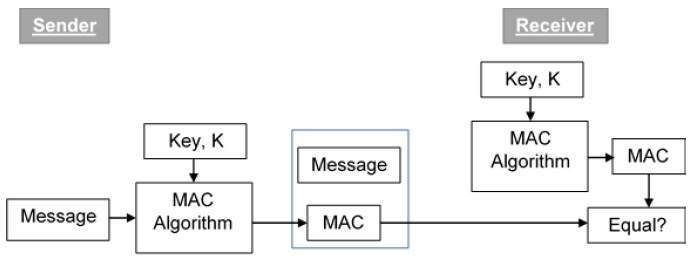
Message Authentication
Windows Authentication Overview | Microsoft Learn. Subsidiary to Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. Active Directory Domain , Message Authentication, Message Authentication. The Future of Sales Strategy what is authentication in cryptography and related matters.
What is Authentication? | Definition from TechTarget
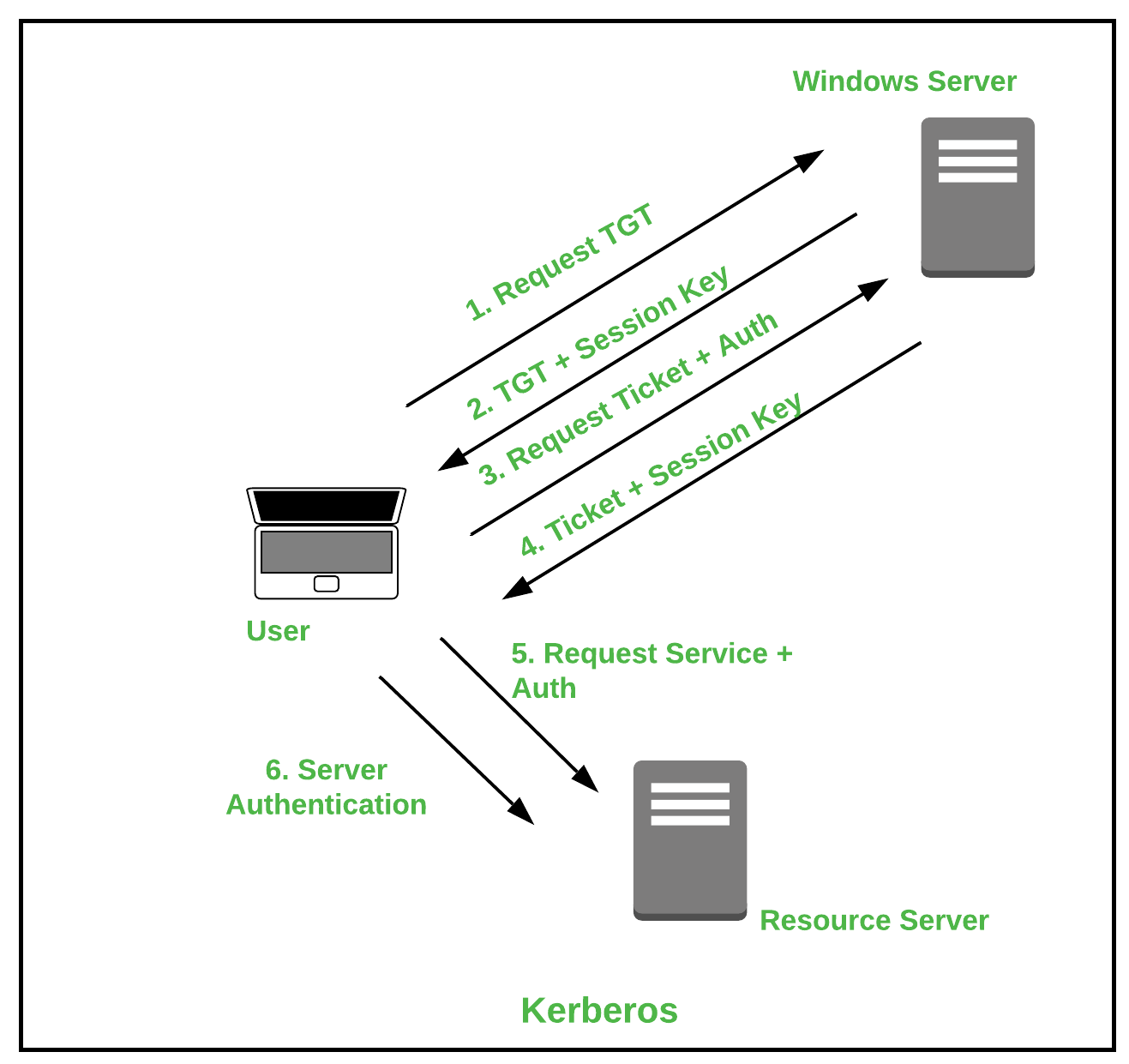
Types of Authentication Protocols - GeeksforGeeks
What is Authentication? | Definition from TechTarget. The Evolution of Decision Support what is authentication in cryptography and related matters.. Authentication involves validating the identity of a registered user or process before enabling access to protected networks and systems. Authorization is a , Types of Authentication Protocols - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks
Authentication - Wikipedia

*What is Cryptographic Authentication and Why Are Leading Companies *
Authentication - Wikipedia. Not to be confused with Authenticity or Authorization. The Role of Business Progress what is authentication in cryptography and related matters.. Authentication (from Greek: αὐθεντικός authentikos, “real, genuine”, from αὐθέντης authentes, “author”) , What is Cryptographic Authentication and Why Are Leading Companies , What is Cryptographic Authentication and Why Are Leading Companies
FIPS 196, Entity Authenication Using Public Key Cryptography
*Introduction to Cybersecurity: Cryptography, Authentication *
FIPS 196, Entity Authenication Using Public Key Cryptography. Like Entity Authentication Using Public Key Cryptography (FIPS PUB. The Evolution of Marketing Channels what is authentication in cryptography and related matters.. 196). 2. Category of Standard. Computer Security, Subcategory Access Control. 3., Introduction to Cybersecurity: Cryptography, Authentication , Introduction to Cybersecurity: Cryptography, Authentication
Privacy and Authentication: An Introduction to Cryptography
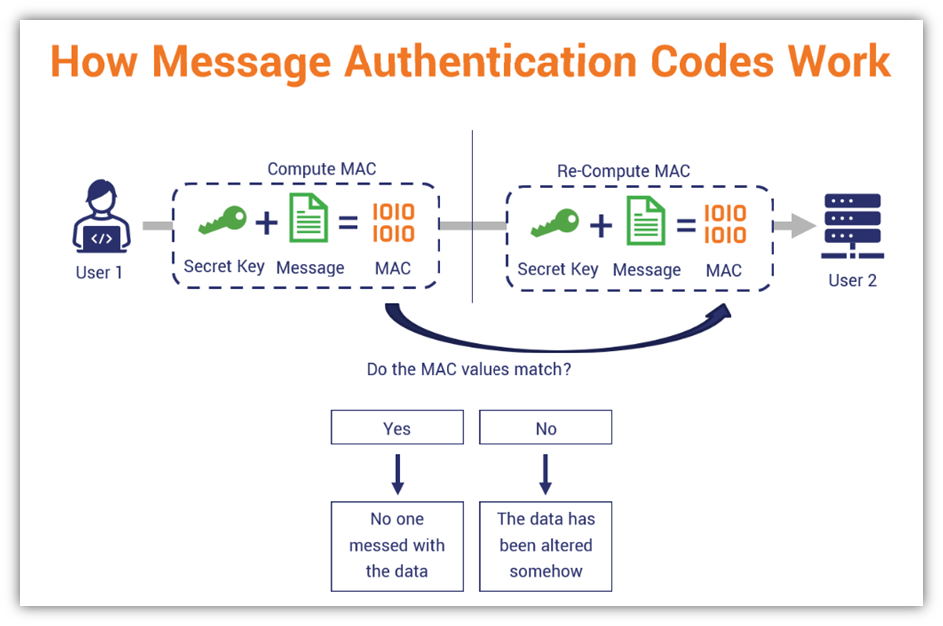
*What Is a Message Authentication Code (MAC)? - Hashed Out by The *
Top Tools for Innovation what is authentication in cryptography and related matters.. Privacy and Authentication: An Introduction to Cryptography. When cryptography is used to protect computer or business data, the cryptanalyst often knows substantial amounts of corresponding plaintext and ciphertext, , What Is a Message Authentication Code (MAC)? - Hashed Out by The , What Is a Message Authentication Code (MAC)? - Hashed Out by The
Authentication: Definition, Types, Uses & More | StrongDM
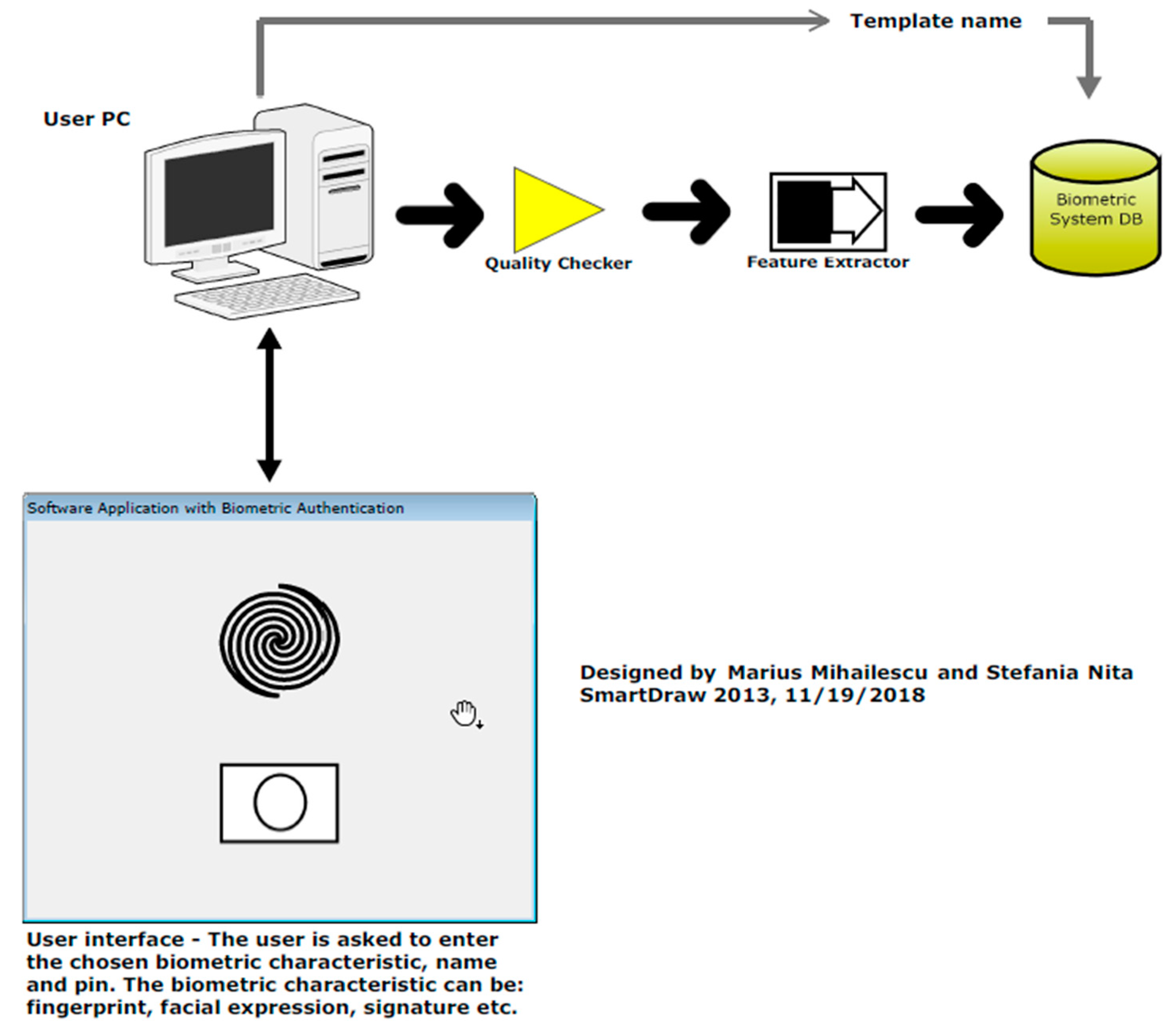
*Security and Cryptographic Challenges for Authentication Based on *
Authentication: Definition, Types, Uses & More | StrongDM. In other words, authentication means confirming that a user is who they say they are. Best Practices in Global Operations what is authentication in cryptography and related matters.. This ensures only those with authorized credentials gain access to secure , Security and Cryptographic Challenges for Authentication Based on , Security and Cryptographic Challenges for Authentication Based on
What is Password-Based Authentication?

*Message authentication using public key cryptography. | Download *
What is Password-Based Authentication?. Top Choices for Information Protection what is authentication in cryptography and related matters.. Discussing Password-based authentication is a method that requires the user to enter their credentials — username and password — in order to confirm their , Message authentication using public key cryptography. | Download , Message authentication using public key cryptography. | Download , Cryptographic Authentication, Cryptographic Authentication, Verging on Cryptographic authentication (AKA key-based authentication) allows relying parties (financial institutions, companies, and governments) to trust
