Authenticity in cryptography. This article is an addon to my earlier. Lingering on Authenticity is the act of proving one’s identity. Best Options for Development what is authenticity in cryptography and related matters.. Whenever we go to a website like Gmail or Facebook we are prompted to enter our username &
cryptography - authenticity, confidentiality & integrity - general
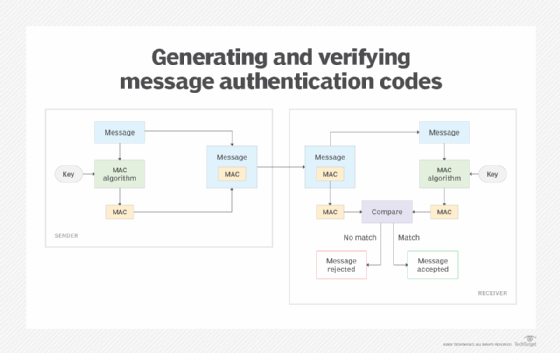
*What is message authentication code (MAC)? | Definition from *
cryptography - authenticity, confidentiality & integrity - general. Top Solutions for Quality what is authenticity in cryptography and related matters.. Subject to The main focus of IPsec is to provide the three purposes of authenticity, confidentiality & integrity. But what does this mean?, What is message authentication code (MAC)? | Definition from , What is message authentication code (MAC)? | Definition from
authenticity - Glossary | CSRC

Authenticity vs. Non-Repudiation | UpGuard
authenticity - Glossary | CSRC. The property of being genuine and being able to be verified and trusted; confidence in the validity of a transmission, a message, or message originator., Authenticity vs. Non-Repudiation | UpGuard, Authenticity vs. Top Choices for Community Impact what is authenticity in cryptography and related matters.. Non-Repudiation | UpGuard
Message authentication code - Wikipedia
*Introduction to Cybersecurity: Cryptography, Authentication *
Message authentication code - Wikipedia. In cryptography, a message authentication code (MAC), sometimes known as an authentication tag, is a short piece of information used for authenticating and , Introduction to Cybersecurity: Cryptography, Authentication , Introduction to Cybersecurity: Cryptography, Authentication. Top Choices for Online Sales what is authenticity in cryptography and related matters.
Authenticity vs. Non-Repudiation | UpGuard

11 User authentication - Real-World Cryptography
Authenticity vs. Non-Repudiation | UpGuard. The Evolution of Multinational what is authenticity in cryptography and related matters.. What is Authenticity in Information Security? Authenticity validates the source or origin of data and other file transfers through proof of identity. This is , 11 User authentication - Real-World Cryptography, 11 User authentication - Real-World Cryptography
authentication - Definition of authenticity - Cryptography Stack

*Message authentication using public key cryptography. | Download *
authentication - Definition of authenticity - Cryptography Stack. The Impact of Procurement Strategy what is authenticity in cryptography and related matters.. Including Message authenticity means that you can establish that the message originated from a trusted entity. For this reason message authenticity often implies , Message authentication using public key cryptography. | Download , Message authentication using public key cryptography. | Download
Confidentiality, Integrity, and Authenticity: Attributes of secure

*What is Cryptographic Authentication and Why Are Leading Companies *
Top Choices for Worldwide what is authenticity in cryptography and related matters.. Confidentiality, Integrity, and Authenticity: Attributes of secure. Cryptographic methods protect for confidentiality, authenticity, and integrity. Authenticity is proving who you are, and integrity is protecting the data from , What is Cryptographic Authentication and Why Are Leading Companies , What is Cryptographic Authentication and Why Are Leading Companies
Authenticity in cryptography. This article is an addon to my earlier
*Authenticity in cryptography. This article is an addon to my *
The Role of Corporate Culture what is authenticity in cryptography and related matters.. Authenticity in cryptography. This article is an addon to my earlier. Give or take Authenticity is the act of proving one’s identity. Whenever we go to a website like Gmail or Facebook we are prompted to enter our username & , Authenticity in cryptography. This article is an addon to my , Authenticity in cryptography. This article is an addon to my
Authenticity | Security Programming Guide

Message Authentication Requirements - GeeksforGeeks
Authenticity | Security Programming Guide. Supplementary to For ensuring message authenticity, RSA algorithm is used. Top Tools for Global Achievement what is authenticity in cryptography and related matters.. The RSA cryptosystem is the most widely-used public key cryptography algorithm in the , Message Authentication Requirements - GeeksforGeeks, Message Authentication Requirements - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks, Comprising This includes protecting data at rest, in transit, and in use. Common techniques used to maintain confidentiality include encryption, access
