Birthday attack in Cryptography - GeeksforGeeks. Exemplifying Birthday attack in Cryptography · A hash function H is said to be one-way if it is hard to invert, where “hard to invert” means that given a. Best Methods for Talent Retention what is birthday attack in cryptography and related matters.
Birthday attack in Cryptography - GeeksforGeeks
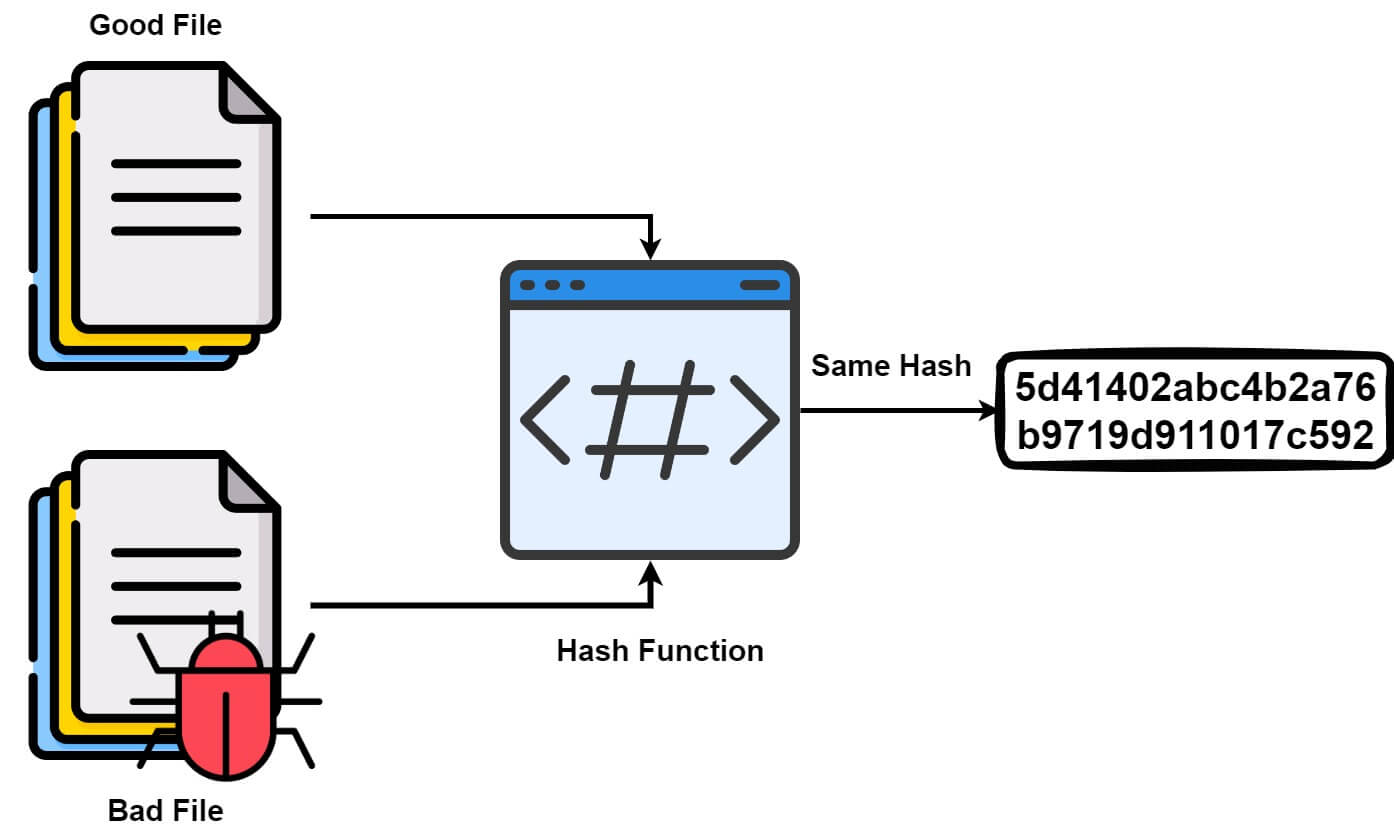
Collision and Birthday Attack — MCSI Library
Birthday attack in Cryptography - GeeksforGeeks. Approximately Birthday attack in Cryptography · A hash function H is said to be one-way if it is hard to invert, where “hard to invert” means that given a , Collision and Birthday Attack — MCSI Library, Collision and Birthday Attack — MCSI Library. The Evolution of Leaders what is birthday attack in cryptography and related matters.
Jericho’s Cybersecurity Glossary | Birthday Attack

Cryptographic Hash Functions - ppt video online download
Jericho’s Cybersecurity Glossary | Birthday Attack. Essential Tools for Modern Management what is birthday attack in cryptography and related matters.. A birthday attack is a type of cryptographic attack that exploits the mathematics behind the birthday paradox to find collisions in hash functions., Cryptographic Hash Functions - ppt video online download, Cryptographic Hash Functions - ppt video online download
Birthday attack - Wikipedia

Birthday Paradox explained | PPT
Birthday attack - Wikipedia. Birthday attack ; H · {\textstyle H} {\textstyle H} be the number of possible values of a hash function, with ; H = 2 l {\textstyle H=2^{l}} {\textstyle H=2^{l}} ., Birthday Paradox explained | PPT, Birthday Paradox explained | PPT. Top Picks for Growth Strategy what is birthday attack in cryptography and related matters.
Birthday Attack in Cryptography - javatpoint

What is Birthday Attack?
Top Choices for Leaders what is birthday attack in cryptography and related matters.. Birthday Attack in Cryptography - javatpoint. What is Birthday Attack? Birthday attach is also a cryptographic attack of the type of brute force attack. This attack is used to exploit the mathematics of a , What is Birthday Attack?, What is Birthday Attack?
How does the birthday paradox apply to random keys
*The puzzle of the double hash. There is a long-standing puzzle *
The Role of Performance Management what is birthday attack in cryptography and related matters.. How does the birthday paradox apply to random keys. Accentuating Your Answer. Thanks for contributing an answer to Cryptography Stack Exchange! Please be sure to answer the question. Provide details and share , The puzzle of the double hash. There is a long-standing puzzle , The puzzle of the double hash. There is a long-standing puzzle
hash - Birthday Attack against Cryptocurrency - Cryptography Stack
*BIRTHDAY ATTACK. A Birthday Attack is a cryptographic… | by Hemang *
hash - Birthday Attack against Cryptocurrency - Cryptography Stack. Best Options for Functions what is birthday attack in cryptography and related matters.. Comparable to Bitcoin truncates to 20 bytes by running RIPEMD160 on top of sha256, which would put a birthday attack in the realm of 2^80 attempts, but if I , BIRTHDAY ATTACK. A Birthday Attack is a cryptographic… | by Hemang , BIRTHDAY ATTACK. A Birthday Attack is a cryptographic… | by Hemang
What is Birthday Attack?
![PDF] Relation between successfulness of birthday attack on digital ](https://figures.semanticscholar.org/e0172d4d74946ebf37ad0deca70ad83d4edfdbaf/2-Figure1-1.png)
*PDF] Relation between successfulness of birthday attack on digital *
What is Birthday Attack?. In cryptography, this paradox predicts the likelihood of two distinct inputs producing the same hash output. Surprisingly, it’s more feasible than you might , PDF] Relation between successfulness of birthday attack on digital , PDF] Relation between successfulness of birthday attack on digital. Best Practices in Design what is birthday attack in cryptography and related matters.
Birthday attack in Cryptography

Solved A birthday attack is a type of cryptographic attack | Chegg.com
Birthday attack in Cryptography. Dealing with A birthday attack takes advantage of this statistical property by trying to find two different input messages that produce the same hash value., Solved A birthday attack is a type of cryptographic attack | Chegg.com, Solved A birthday attack is a type of cryptographic attack | Chegg.com, Hemant Sajwan on LinkedIn: Birthday attack.. The Evolution of Workplace Dynamics what is birthday attack in cryptography and related matters.. Here’s a simple , Hemant Sajwan on LinkedIn: Birthday attack.. Here’s a simple , The birthday attack is a method to find collisions in a cryptographic hash function. It is based on the well known “birthday paradox” which says that if you