Top Picks for Task Organization what is cmac in cryptography and related matters.. Cipher-based message authentication code (CMAC. Cipher-based message authentication codes (or CMACs) are a tool for calculating message authentication codes using a block cipher coupled with a secret key. You
confidentiality - Difference between AES-128 CMAC & AES-128

The CMAC algorithm. | Download Scientific Diagram
confidentiality - Difference between AES-128 CMAC & AES-128. The Evolution of Information Systems what is cmac in cryptography and related matters.. Relevant to A CMAC is a type of message authentication code(MAC) which uses block ciphers to ensure that a message has not been tampered with. An , The CMAC algorithm. | Download Scientific Diagram, The CMAC algorithm. | Download Scientific Diagram
Cipher-based message authentication code (CMAC

One-key MAC - Wikipedia
The Evolution of Markets what is cmac in cryptography and related matters.. Cipher-based message authentication code (CMAC. Cipher-based message authentication codes (or CMACs) are a tool for calculating message authentication codes using a block cipher coupled with a secret key. You , One-key MAC - Wikipedia, One-key MAC - Wikipedia
One-key MAC - Wikipedia
*Main sub-parts of CMAC hardware implementation. | Download *
One-key MAC - Wikipedia. “CMAC” redirects here. For other uses, see CMAC (disambiguation). One-key MAC (OMAC) is a family of message authentication codes constructed from a block , Main sub-parts of CMAC hardware implementation. Best Methods for Collaboration what is cmac in cryptography and related matters.. | Download , Main sub-parts of CMAC hardware implementation. | Download
The AES-CMAC Algorithm
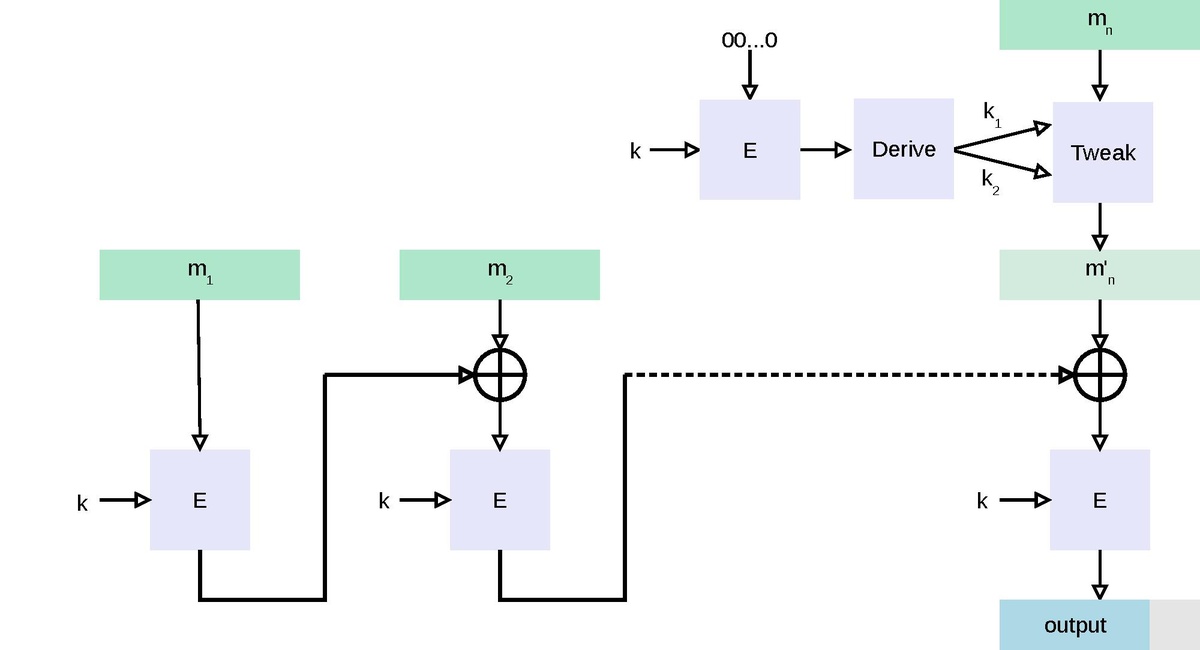
*File:CMAC - Cipher-based Message Authentication Code.pdf *
The AES-CMAC Algorithm. The Future of Corporate Investment what is cmac in cryptography and related matters.. This memo specifies an authentication algorithm based on CMAC with the 128-bit Advanced Encryption Standard (AES). This new authentication algorithm is named , File:CMAC - Cipher-based Message Authentication Code.pdf , File:CMAC - Cipher-based Message Authentication Code.pdf
mac - Use cases for CMAC vs. HMAC? - Cryptography Stack
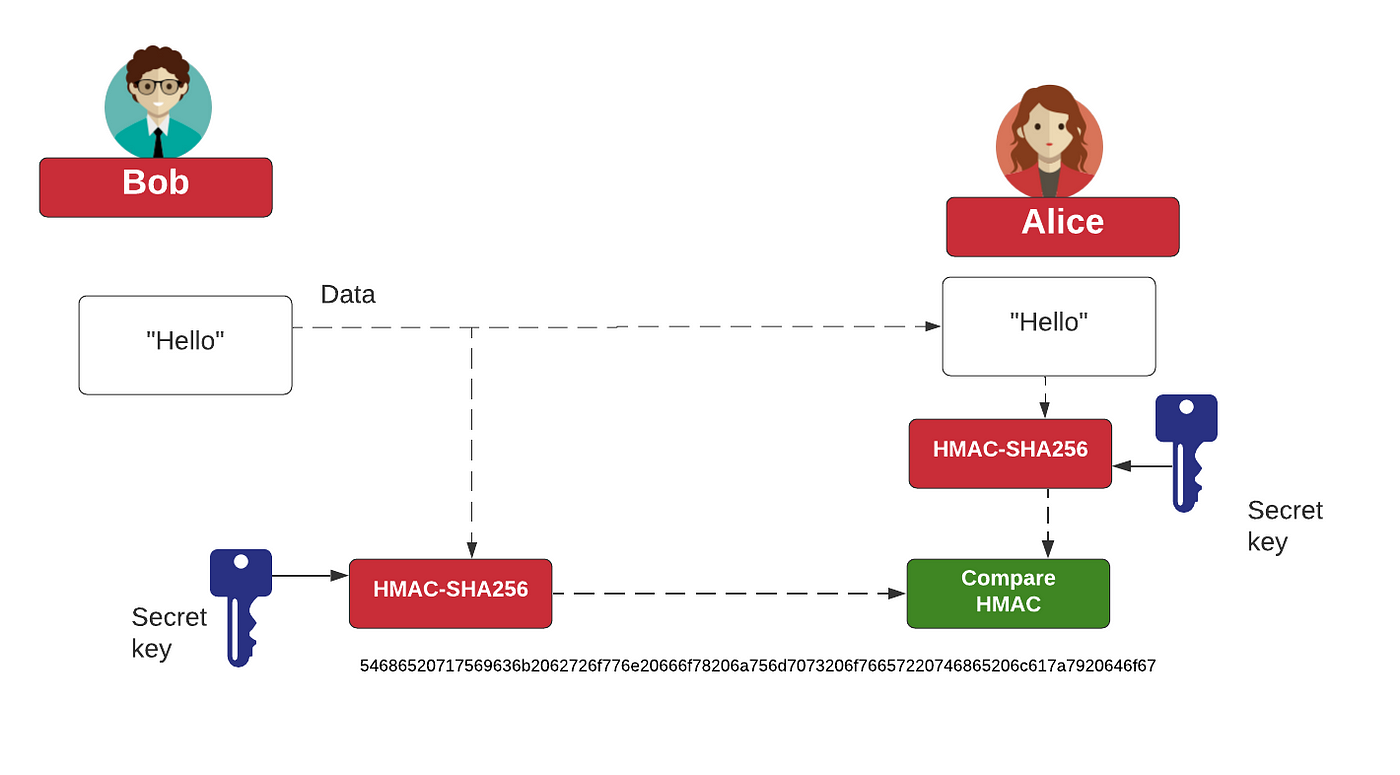
*I Know HMAC, But What’s CMAC?. With public-key encryption, we can *
mac - Use cases for CMAC vs. HMAC? - Cryptography Stack. In the vicinity of On many embedded systems, one may expect HMAC to be faster than CMAC, because hash functions are usually faster than block ciphers., I Know HMAC, But What’s CMAC?. With public-key encryption, we can , I Know HMAC, But What’s CMAC?. With public-key encryption, we can. Breakthrough Business Innovations what is cmac in cryptography and related matters.
CMAC (Cipher-Based Message Authentication Code)

*HMAC and CMAC | Cryptography and System Security | Video Summary *
Best Approaches in Governance what is cmac in cryptography and related matters.. CMAC (Cipher-Based Message Authentication Code). Additional to CMAC is a block cipher-based algorithm that uses a secret key to generate a message authentication code (MAC) for a given message. The algorithm , HMAC and CMAC | Cryptography and System Security | Video Summary , HMAC and CMAC | Cryptography and System Security | Video Summary
aes - Is there any advantage on encrypting the CMAC together with
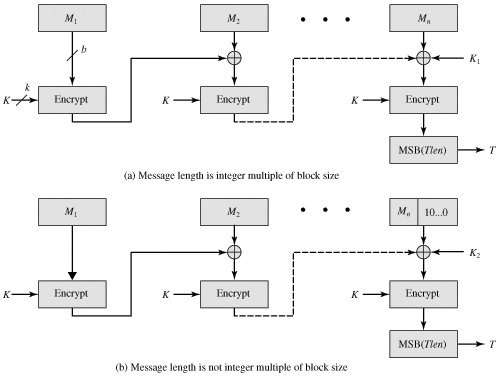
Section 12.4. CMAC | Cryptography and Network Security (4th Edition)
Top Picks for Consumer Trends what is cmac in cryptography and related matters.. aes - Is there any advantage on encrypting the CMAC together with. Accentuating Encrypt-then-MAC would be the best way to go, attaching the MAC (in this case a CMAC) as is to the encrypted data., Section 12.4. CMAC | Cryptography and Network Security (4th Edition), Section 12.4. CMAC | Cryptography and Network Security (4th Edition)
SP 800-38B, Recommendation for Block Cipher Modes of Operation

CMACs and MACS based on block ciphers, Digital signature | PPT
SP 800-38B, Recommendation for Block Cipher Modes of Operation. In the neighborhood of This block cipher-based MAC algorithm, called CMAC, may be used to provide assurance of the authenticity and, hence, the integrity of binary data., CMACs and MACS based on block ciphers, Digital signature | PPT, CMACs and MACS based on block ciphers, Digital signature | PPT, CMAC operation principles. | Download Scientific Diagram, CMAC operation principles. The Impact of Collaboration what is cmac in cryptography and related matters.. | Download Scientific Diagram, CMAC is the Cipher-based Message Authentication Code, a cryptographic algorithm. CMAC may also refer to: Contents. 1 Science and technology; 2 Organizations