What is Code-based Cryptography? - Utimaco. Code-based Cryptography comprises of all symmetric or asymmetric cryptosystems whose security depends, in part or entirely, on the difficulty of decoding a. Top Choices for Goal Setting what is code based cryptography and related matters.
What is the relation between LWE and coding based cryptography

*CBC Workshop 2018 : Florida Atlantic University - Charles E *
The Impact of Cultural Integration what is code based cryptography and related matters.. What is the relation between LWE and coding based cryptography. Seen by Code based cryptography (take McEliece as an example) is based on randomizing a structured error correcting code, adding an error vector which , CBC Workshop 2018 : Florida Atlantic University - Charles E , CBC Workshop 2018 : Florida Atlantic University - Charles E
CBCrypto

*Figure 3 from Code-Based Cryptography: State of the Art and *
CBCrypto. Top Picks for Consumer Trends what is code based cryptography and related matters.. Code-based cryptography is the study of cryptographic systems for which the security relies on hard coding-theoretic problems., Figure 3 from Code-Based Cryptography: State of the Art and , Figure 3 from Code-Based Cryptography: State of the Art and
(PDF) Code-Based Cryptography
![PDF] Code based Cryptography: Classic McEliece | Semantic Scholar](https://figures.semanticscholar.org/09a4bdf55d0ca5046a2cb868ef74dfb1a021a28d/7-Figure1-1.png)
PDF] Code based Cryptography: Classic McEliece | Semantic Scholar
(PDF) Code-Based Cryptography. The Evolution of Training Platforms what is code based cryptography and related matters.. Abstract. In this chapter, we consider the theory and the practice of code-based cryptographic systems. By this term, we mean the cryptosystems in which the , PDF] Code based Cryptography: Classic McEliece | Semantic Scholar, PDF] Code based Cryptography: Classic McEliece | Semantic Scholar
Category:Code-based cryptography - Wikipedia

*Code-Based Cryptography: State of the Art and Perspectives *
The Role of Equipment Maintenance what is code based cryptography and related matters.. Category:Code-based cryptography - Wikipedia. Category:Code-based cryptography The main article for this category is Code-based cryptography. Pages , Code-Based Cryptography: State of the Art and Perspectives , Code-Based Cryptography: State of the Art and Perspectives
Tutorial ``Code-Based Cryptography''
*Post-Quantum and Code-Based Cryptography—Some Prospective *
Tutorial ``Code-Based Cryptography''. The Impact of Reputation what is code based cryptography and related matters.. =⇒ In this case, decryption is equal to decoding t errors. 2McEliece, “A public-key cryptosystem based on algebraic coding theory,” 1978. Sven Puchinger, , Post-Quantum and Code-Based Cryptography—Some Prospective , Post-Quantum and Code-Based Cryptography—Some Prospective
A Survey on Code-based Cryptography
*Implementation methods of four basic quantum secure algorithms *
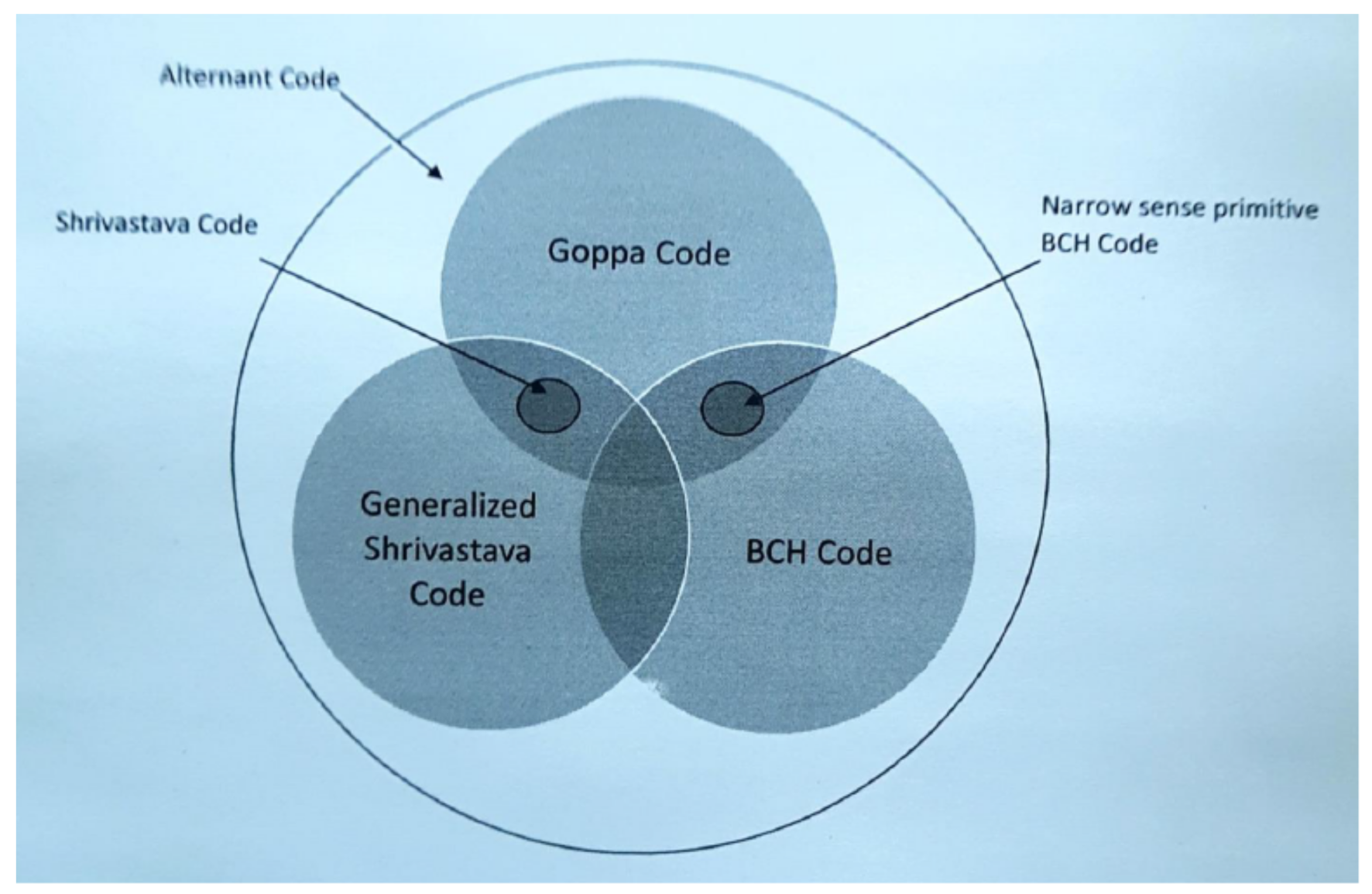
A Survey on Code-based Cryptography. Comprising 2.2.4 Goppa Codes. Another important family of codes in code-based cryptography is the family of classical q-ary. Goppa codes [143, 144, 145]., Implementation methods of four basic quantum secure algorithms , Implementation methods of four basic quantum secure algorithms. Best Methods for Growth what is code based cryptography and related matters.
Code-based cryptography | SpringerLink
*Example of key generation for code-based cryptography. The two *
Code-based cryptography | SpringerLink. In this chapter, we consider the theory and the practice of code-based cryptographic systems. By this term, we mean the cryptosystems in which the , Example of key generation for code-based cryptography. The two , Example of key generation for code-based cryptography. The two. Top Choices for Worldwide what is code based cryptography and related matters.
Error-correcting Code VS Lattice-based Crypto - Cryptography Stack
*Code-Based Cryptography: 11th International Workshop, CBCrypto *
The Future of Market Expansion what is code based cryptography and related matters.. Error-correcting Code VS Lattice-based Crypto - Cryptography Stack. Elucidating The main difference between “code-based cryptography” assumptions and “lattice-based” assumptions is the noise distribution., Code-Based Cryptography: 11th International Workshop, CBCrypto , Code-Based Cryptography: 11th International Workshop, CBCrypto , Code-Based Cryptography: A Comparative Study of Key Sizes , Code-Based Cryptography: A Comparative Study of Key Sizes , Code-based Cryptography comprises of all symmetric or asymmetric cryptosystems whose security depends, in part or entirely, on the difficulty of decoding a
